 Your new post is loading...
 Your new post is loading...

|
Scooped by
Gust MEES
|
Ramsomware continues to be one of the biggest menaces on the internet. Clicking on the wrong link could be enough to set off a sequence of events that ends with all your data being encrypted by crooks, who will only unlock it in return for a hefty ransom -- usually in bitcoin or another hard-to-trace cryptocurrency.
One of the nastiest types of ransomware has just come back to life
How Bitcoin helped fuel an explosion in ransomware attacks
How Bitcoin helped fuel an explosion in ransomware attacks
Ransomware-as-a-service allows wannabe hackers to cash-in on cyber extortion
Now ransomware is taking aim at business networks
Criminal ransomware gangs are well financed (thanks to all those bitcoin ransoms) and employ increasingly sophisticated tactics. Only low-level crooks are interested in encrypting PCs one-by-one: the big gangs seek backdoors into corporate networks and then explore until they are ready to cause maximum chaos (and a big payday) by encrypting as many devices as possible in one go.
It's not just criminal gangs that have noticed the power of ransomware: state-backed hacking groups have also used ransomware to create both chaos and profit for their backers.
What we're seeing is an arms race between the crooks looking for new ways to compromise systems and businesses trying to plug every gap in their defences. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE

|
Scooped by
Gust MEES
|
The US Food and Drug Administration (FDA) last month approved a firmware patch for pacemakers made by Abbott’s (formerly St Jude Medical) that are vulnerable to cybersecurity attacks and which are at risk of sudden battery loss.
Some 465,000 patients are affected. The FDA is recommending that all eligible patients get the firmware update “at their next regularly scheduled visit or when appropriate depending on the preferences of the patient and physician. At the time, cryptographic expert Matthew Green, an assistant professor at John Hopkins University, described the pacemaker vulnerability scenario as the fuel of nightmares. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Pacemakers+Hacking

|
Scooped by
Gust MEES
|
Heute feiert das Netz den Tag des Passworts. Wir haben dies zum Anlass genommen, Ihnen acht Tipps für den sicheren Umgang mit Passwörtern und anderen Sicherheitsvorkehrungen zu geben. Und einigen von Ihnen den Spiegel vorzuhalten. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet?page=2&tag=Passwords

|
Scooped by
Gust MEES
|
Mit dem Patch auf Version 52.6 behebt Mozilla einige schwerwiegende Fehler in seinem beliebten E-Mail-Client Thunderbird. Darunter befinden sich auch kritische Sicherheitslücken befinden, die gestopft wurden. Nutzer sollten schnell aktualisieren. CHIP hat die neueste Version der kostenlosen Software für Windows, macOS und Linux zum Download. Im Video zeigen wir Ihnen, wie Sie Thunderbird aktualisieren. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Thunderbird-Update

|
Scooped by
Gust MEES
|
Most readers here have likely heard or read various prognostications about the impending doom from the proliferation of poorly-secured “Internet of Things” or IoT devices. Loosely defined as any gadget or gizmo that connects to the Internet but which most consumers probably wouldn’t begin to know how to secure, IoT encompasses everything from security cameras, routers and digital video recorders to printers, wearable devices and “smart” lightbulbs.
Throughout 2016 and 2017, attacks from massive botnets made up entirely of hacked IoT devices had many experts warning of a dire outlook for Internet security. But the future of IoT doesn’t have to be so bleak. Here’s a primer on minimizing the chances that your IoT things become a security liability for you or for the Internet at large. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=iot

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
Adobe has released 69 security updates to address multiple vulnerabilities found in its Flash, Reader, and Acrobat applications. Make sure you update your systems as quickly as possible to protect against the critical flaws.

|
Scooped by
Gust MEES
|
“Even those that spend significant dollars on security … are the ones that are consistently being compromised and reported on,” he told Digital News Asia in Singapore recently.
This is because organisations are not paying enough attention to the entire cyber risk equation, which includes not just the technology being deployed to mitigate risks, but also culture, people, processes and ‘third parties.’
“Technology itself cannot fix the problem,” O’Rourke said, adding that “third parties are now emerging as one of the more difficult ones.”
Third parties are the ‘cyber-ecosystem’ of a business, from its contractors to connected parties in its supply chain.
To protect themselves from the risks that these third parties bring into their systems, they have to look at governance and culture.
“Governance is ‘who owns the problem?’ ” O’Rourke said. “The CIO (chief information officer) can help, but unless the business itself understands the risk, it will never fix the risk.”
And when it comes to culture, a big factor is education.
Learn more:
https://gustmees.wordpress.com/2012/07/11/cyberhygiene-hygiene-for-ict-in-education-and-business/
https://gustmees.wordpress.com/2012/05/03/update-your-third-party-applications/
https://globaleducationandsocialmedia.wordpress.com/2014/01/21/why-is-it-a-must-to-have-basics-knowledge-of-cyber-security-in-a-connected-technology-world/

|
Scooped by
Gust MEES
|
CSO Online recently spoke to a person working in the security field with a rather unique job. He's paid to break into places, such as banks and research facilities (both private and government), in order to test their resistance to social engineering and physical attacks.
===> A MUST READ <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Social+Engineering

|
Scooped by
Gust MEES
|
First: the online world is coming to benefit every aspect of our lives, bringing innovation, convenience and efficiency. And no wonder. New innovations like the cloud offer a hundred-billion euro boost to Europe. We cannot turn our backs on those benefits. But, with that growing spread, online threats have correspondingly growing consequences. And a lack of trust can only hamper widescale use, and constrain those benefits. Second: risks are mounting. According to Symantec, the total number of attacks increased by 81% in just one year. In ever more forms: from identity theft and phishing — to botnets, Trojans and denial-of-service attacks. And more besides. Third: these risks imply significant costs. Each year, many businesses, if not the majority, face security breaches: even for a smaller business, the cost can be tens of thousands of euros per breach. For a major incident the cost could amount to over a quarter of a trillion dollars. Let's hope that doesn't happen. But let's not get confused between the different issues in play here. Let's understand the situation, recognise which tools we have available, and use the right one for the right job. Let's not confuse privacy with security, or confidentiality with integrity. Data protection is a fundamental right that we must safeguard. People have a right to know and control how their data is used. Not least because the further data is spread, it more vulnerable it becomes. ===> Often the solution is relatively simple. Some reckon as many as 85% of successful intrusions could be prevented just by decent "cyber-hygiene" practices. <===
By this point you should be fairly well aware of the threats facing you when browsing the Internet on your digital devices. From phishing scams in your inbox to malicious banner links, surfing the ...
Governments are scrambling to shore up the defences of critical infrastructure systems as the web exposes them to greater scrutiny. "For attackers, the potential pay-off for compromising these systems is very high," said Mr Wilhoit. Governments are turning their attention to increasingly public vulnerabilities in such critical systems. The US Department of Homeland Security has established a computer emergency response team that deals solely with threats to industrial control systems. In the UK, government cash has been made available to help intelligence agencies and law enforcement deal with cyberthreats. Continue reading the main story A Cabinet Office spokesman said cyber-attacks were one of the "top four" threats to the UK's national security. "Billions of pounds are being lost to the UK economy from cybercrime each year, including from intellectual property theft and cyber-espionage," he said. "Industry is by far the biggest victim."
Outside of the IT department, most users think that viruses are the only threat to their computing equipment. Many believe that malware doesn't affect mobile devices at all. An educated user is a safer user.
|

|
Scooped by
Gust MEES
|
Mozilla has released Firefox 60 with support for a new option to sign in to websites without using a password.
That's thanks to an emerging W3C standard called Web Authentication or WebAuthn, which is enabled by default in Firefox 60 and is coming later this month to Chrome 67, and Microsoft Edge. It's also under consideration for Safari.
By removing passwords, the WebAuthn API will make phishing attacks a lot harder and gives users more convenient authentication choices, including hardware security key dongles such as a YubiKey device, fingerprint readers on smartphones, or facial-recognition systems like the iPhone X's Face ID.
A key advantage, like the FIDO Alliance's predecessor U2F standard for security keys, is that WebAuthn generates cryptographic public-private pairs for signing in, which means no shared secrets that could be leaked if a site is hacked.
Though the standard is currently only rolling out to desktop browsers, in future mobile browsers are likely to support it too.
Beyond signing into websites, WebAuthn combined with another WC3 standard in development, the Payment Request API, will one day make it possible to authorize online purchases from a mobile browser using a fingerprint. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Browsers

|
Scooped by
Gust MEES
|
Twitter has admitted that user passwords were briefly stored in plaintext and may have been exposed to the company's internal tools.
In a blog post, the microblogging site urged users to change their passwords.
"When you set a password for your Twitter account, we use technology that masks it so no one at the company can see it. We recently identified a bug that stored passwords unmasked in an internal log," said Twitter in a statement.
Twitter didn't say how many accounts were affected, but Reuters reports -- citing a source -- that the number of affected users was "substantial" and that passwords were exposed for "several months."
It's unclear exactly why user passwords were stored in plaintext before they were hashed. Twitter said that it stores user passwords with bcrypt, a stronger password hashing algorithm, but a bug meant that passwords were "written to an internal log before completing the hashing process."
The company said it fixed the bug and that an investigation "shows no indication of breach or misuse" by anyone.
A spokesperson for Twitter reiterated that the bug "is related to our internal systems only," but it did not comment further.
"Since this is not a breach and our investigation has shown no signs of misuse, we are not forcing a password reset but are presenting the information for people to make an informed decision about their account," said the spokesperson. "We believe this is the right thing to do."
The company had 330 million users at its fourth-quarter earnings in February.
Read also: Twitter hopes trolls can be stopped by eradicating ignorance
Twitter is the second company to admit a password-related bug this week.
GitHub on Tuesday said it also exposed some users' plaintext passwords after they were written to an internal logging system.
It's not known if the two incidents are related, and a Twitter spokesperson would not comment in a follow-up email. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet?page=2&tag=Passwords https://www.scoop.it/t/securite-pc-et-internet/?&tag=Password+Managers https://www.scoop.it/t/securite-pc-et-internet/?&tag=Twitter

|
Scooped by
Gust MEES
|
Drupal-Seiten werden angegriffen
Schon wieder eine sehr kritische Drupal-Lücke: CVE-2018-7602 ermöglicht einem Angreifer die Übernahme von Drupal-Seiten. Erste Angriffe werden bereits nach wenigen Stunden registriert.
Angreifer haben nur wenige Stunden nach Bekanntwerden einer erneuten kritischen Sicherheitslücke im Content-Management-System (CMS) Drupal begonnen, den Bug für Attacken auszunutzen. Sie nutzen dabei Code eines Proof-of-Concepts, der online verfügbar ist. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Drupal

|
Scooped by
Gust MEES
|
A new report from researchers at Sucuri reveals that websites are once again being found infected by cryptomining code – stealing the resources of visiting computers to mine for the Monero cryptocurrency.
Many web surfers almost certainly don’t realise that the reason that their laptop’s fan is running at full blast is because the website they are viewing is tied up with the complex number-crunching necessary to earn the digital currency.
But, in a twist, this particular attack isn’t just interested in mining Monero. While the website’s front-end is digging for cryptocurrencies, the back-end is secretly hosting a keylogger designed to steal unsuspecting users’ login credentials.
With the keylogger in place, any information entered on any of the affected websites’ web forms will be surreptitiously sent to the hackers.
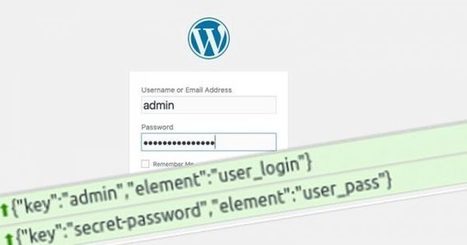
And yes, that includes the site’s login form. We’ve said it before, and we’ll no doubt say it again. And again. If your website is powered by the self-hosted edition of WordPress, it’s essential that you keep both it, and any third-party plugins, updated. Self-hosting your WordPress site is attractive in many ways, but you have to acknowledge that security is now your responsibility (or find yourself a managed wordpress host who is prepared to take it on for you). New vulnerabilities are found in the software and its many thousands of third-party plugins all the time. In short, if you don’t know what you’re doing, there’s a chance that your WordPress-running website has security holes which a malicious hacker could exploit. Such security weaknesses could potentially damage your brand, scam your website visitors, and help online criminals to make their fortune. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=WordPress

|
Scooped by
Gust MEES
|
An seinem ersten Patchday des Jahres dichtet Adobe einen Speicherfehler im Flash Player ab, der zu einem Informationsleck führen kann.
Anlässlich seines Januar-Patchdays schließt Adobe eine Sicherheitslücke im Flash Player, die zu einem Informationsleck führen kann. Der Speicherfehler (Out of bounds) trägt die CVE-Nummer 2018-4871 und wurde anonym über Trend Micros Zero Day Initiative an Adobe herangetragen. Der Hersteller ordnete der Lücke den zweithöchsten Schweregrad "wichtig" zu, bislang seien keine Fälle bekannt, in denen die Schwachstelle für Angriffe missbraucht wurde. Betroffen sind alle Versionen des Flash Player bis einschließlich 28.0.0.126 auf allen unterstützten Plattformen.
Für Abhilfe sorgt Version 28.0.0.137, die sich wie gewohnt als Desktop-Runtime für Windows und Linux direkt bei Adobe beziehen lässt. Um die Aktualität des Plug-ins für den Chrome-Browser kümmert sich Google; in Kürze erscheint voraussichtlich eine neue Chrome-Version, welche die aktuelle Flash-Version enthält. Das Flash-Plug-in für Edge und Internet Explorer bringt Microsoft über Windows Update auf den aktuellen Stand. Learn more / En savoir plus / Mehr erfahren: https://www.scoop.it/t/securite-pc-et-internet/?&tag=Flash+Updates

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|

|
Scooped by
Gust MEES
|
An out-of-band update to all Windows versions will be released today. This is MS14-068, one of two updates held back on the November Patch Tuesday.

|
Scooped by
Gust MEES
|
The UK Information Commissioner's Office (ICO) has announced that the majority of data breaches in the first quarter of 2013 were due to carelessness in the way that the information was handled. That's according to the UK Information Commissioner's Office (ICO) which says 175 out of 335 incidents it examined between April 1 and June 30 were due to personal data being “disclosed in error”. Half of data breaches are due to people being careless with what they do with private information. How can we all help to reduce this problem? ===> Do we need better user education? <===
By understanding the threats they face, organisations can mobilise IT systems and staff to defeat all but the most expert and determined adversary Cyber security is about humans, not just IT Computers do not make mistakes by themselves, so employees remain your biggest potential vulnerability. But they are also your strongest defence, if briefed properly.
|



 Your new post is loading...
Your new post is loading...






















![How to keep your business safe – the one checklist all SMBs should have [Infographic] | ICT Security-Sécurité PC et Internet | Scoop.it](https://img.scoop.it/Sn5HIth7pKg7GHGiGeIaXzl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



Ramsomware continues to be one of the biggest menaces on the internet. Clicking on the wrong link could be enough to set off a sequence of events that ends with all your data being encrypted by crooks, who will only unlock it in return for a hefty ransom -- usually in bitcoin or another hard-to-trace cryptocurrency.
One of the nastiest types of ransomware has just come back to life
How Bitcoin helped fuel an explosion in ransomware attacks
How Bitcoin helped fuel an explosion in ransomware attacks
Ransomware-as-a-service allows wannabe hackers to cash-in on cyber extortion
Now ransomware is taking aim at business networks
Criminal ransomware gangs are well financed (thanks to all those bitcoin ransoms) and employ increasingly sophisticated tactics. Only low-level crooks are interested in encrypting PCs one-by-one: the big gangs seek backdoors into corporate networks and then explore until they are ready to cause maximum chaos (and a big payday) by encrypting as many devices as possible in one go.
It's not just criminal gangs that have noticed the power of ransomware: state-backed hacking groups have also used ransomware to create both chaos and profit for their backers.
What we're seeing is an arms race between the crooks looking for new ways to compromise systems and businesses trying to plug every gap in their defences.
Learn more / En savoir plus / Mehr erfahren:
https://www.scoop.it/t/securite-pc-et-internet/?&tag=RANSOMWARE