Bitcoin's sharp rise in value this year has many questioning whether the virtual currency is sustainable in the long term
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
December 11, 2013 6:35 PM
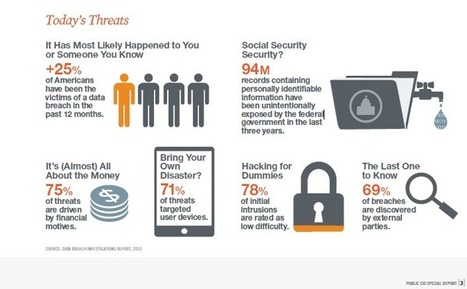
===> And, the team recommended the common-sense step of upgrading WordPress and all plugins to their latest versions. <===
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=WordPress

Gust MEES's curator insight,
November 12, 2013 10:06 AM
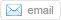
Based off of what we’ve seen at CSID, a credit card number, name and date of birth can sell for $13. A Social Security Number can go for $20. A bank account with a balance of $10,000 goes for an average cost of $625. Even the value of a person’s social media account has worth. According to RSA, 10,000 followers on Twitter sell for $15. 1,000 likes on Facebook sell for $15.
Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Cybercrime...
|

Gust MEES's curator insight,
November 13, 2013 11:13 AM
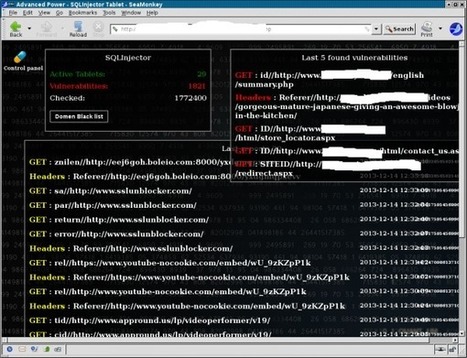
Symantec advises users never share account credentials to any third party applications or services. Third party applications or services that require access to your account or information should use the legitimate APIs and authorization protocols (OAuth 2.0, for instance).
Learn more:
- https://gustmees.wordpress.com/2013/06/23/ict-awareness-what-you-should-know/

Zhao KQiang's curator insight,
March 27, 2014 6:48 AM
one of interesting information, the video shows the security risk in daily life using smart phone. It is easy to call public to aware about the mobile security, also it contains lots of data which are useful |






![What happens after a data breach? [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/mhk80ig_OIgh0szG8FDh-jl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)






Learn more:
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Bitcoin