Bis zu 500 Millionen Android-Smartphones sollen über einen fehlerhaft implementierten "Factory Reset" verfügen. Passwörter und Nutzerdaten seien dadurch auch nach dem Zurücksetzen des Geräts wiederherstellbar.
Research and publish the best content.
Get Started for FREE
Sign up with Facebook Sign up with X
I don't have a Facebook or a X account
Already have an account: Login
Related articles to 21st Century Learning and Teaching as also tools...
Curated by
Gust MEES
 Your new post is loading... Your new post is loading...
 Your new post is loading... Your new post is loading...

Gust MEES's curator insight,
July 4, 2013 6:45 AM
The vulnerability allows hackers to modify an app without breaking its cryptographic signature, according to Jeff Forristal, chief technology officer (CTO) at mobile security firm Bluebox. 
Gust MEES's curator insight,
July 4, 2013 6:48 AM
The vulnerability allows hackers to modify an app without breaking its cryptographic signature, according to Jeff Forristal, chief technology officer (CTO) at mobile security firm Bluebox. 
Zhao KQiang's curator insight,
March 27, 2014 6:52 AM
there is one example of smart phone security. focus on the mobile system Android |
|





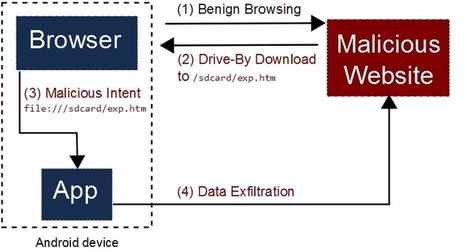







Bis zu 500 Millionen Android-Smartphones sollen über einen fehlerhaft implementierten "Factory Reset" verfügen. Passwörter und Nutzerdaten seien dadurch auch nach dem Zurücksetzen des Geräts wiederherstellbar.