L’ENISA fête cette année ses 10 ans au service de la cyber-sécurité. C’était également l’occasion d’ouvrir le Mois européen de la cyber-sécurité.
Impliquer le citoyen était au cœur du débat mené par François Thill, responsable CASES, membre du conseil d’administration de l’ENISA et coordinateur des activités ECSM pour le Luxembourg.
Le Luxembourg est l’un des pays pilotes en Europe quant à la sensibilisation grand public aux bonnes pratiques des technologies de l’information. Les initiatives telles que CASES, CIRCL et BEE SECURE ont commencé à émerger au Grand-Duché il y a une bonne dizaine d’années déjà. Elles sont aujourd’hui coordonnées par « Security made in Lëtzebuerg » (SMILE), le groupement d'intérêt économique qui a été mandaté en 2010 par le ministère de l'Economie pour renforcer la sécurité de l'information au Grand-Duché de Luxembourg. CASES, CIRCL et BEE SECURE ont pour mission de développer le niveau de savoir-faire de la population en matière d’Internet, en démocratisant les informations, les méthodes et les connaissances existantes. Leur objectif ultime est de faire bénéficier les utilisateurs des opportunités que livre l’Internet dans un climat de confiance et de résilience par rapport aux risques.



 Your new post is loading...
Your new post is loading...




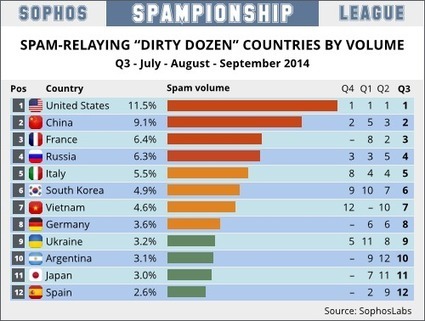




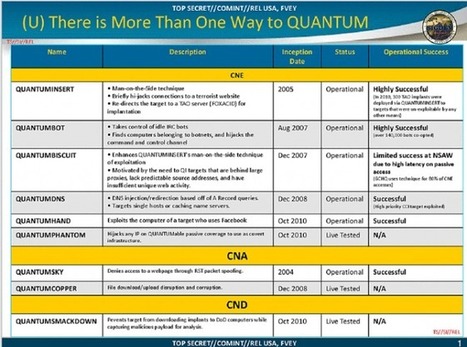

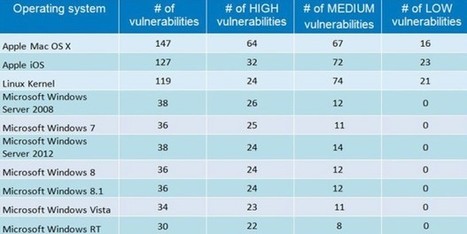



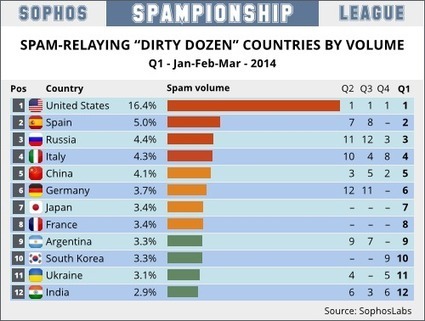
![H1 2014 Threat Report - F-Secure [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/3WKggSg7n-Fjl4tKZAeUKDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)



Learn more on How-To protect (automatically):
- https://gustmees.wordpress.com/2012/05/03/update-your-third-party-applications/