Today the Joint Cybercrime Action Taskforce (J-CAT) is launched to further strengthen the fight against cybercrime in the European Union and beyond. Hosted at the European Cybercrime Centre (EC3) at Europol, the J-CAT, which is being piloted for six months, will coordinate international investigations with partners working side-by-side to take action against key cybercrime threats and top targets, such as underground forums and malware, including banking Trojans. The J-CAT will be led by Andy Archibald, Deputy Director of the National Cyber Crime Unit from the UK’s National Crime Agency (NCA).
The J-CAT was initiated by Europol's EC3, the EU Cybercrime Taskforce, the FBI and the NCA, and the J-CAT comprises a team composed of Cyber Liaison Officers from committed and closely involved Member States, non-EU law enforcement partners and EC3. Key contributors to the intelligence pool will be the EU Member States via EC3, and other law enforcement cooperation partners. Thus far, Austria, Canada, Germany, France, Italy, the Netherlands, Spain, the UK and the US are part of the J-CAT. Australia and Colombia have also committed to the initiative.
Learn more:
- http://gustmees.wordpress.com/2014/08/29/twitter-chat-the-economic-impact-of-cybercrime/



 Your new post is loading...
Your new post is loading...

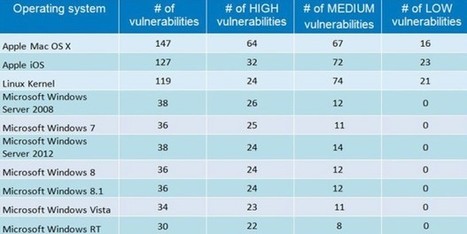





![H1 2014 Threat Report - F-Secure [Infographic] | 21st Century Learning and Teaching | Scoop.it](https://img.scoop.it/3WKggSg7n-Fjl4tKZAeUKDl72eJkfbmt4t8yenImKBVvK0kTmF0xjctABnaLJIm9)












Learn more:
- http://www.scoop.it/t/apple-mac-ios4-ipad-iphone-and-in-security
- http://www.scoop.it/t/securite-pc-et-internet/?tag=Linux